
Managing Director, Netrika Consulting India Pvt Ltd, ASIS APAC Board Member
CFE, CII, FCIISCM, CATS, CCPS, CFAP

Managing Director, Netrika Consulting India Pvt Ltd, ASIS APAC Board Member
CFE, CII, FCIISCM, CATS, CCPS, CFAP

Director - Cyber Security
Information security, often referred to as InfoSec, refers to the processes and tools designed and deployed to protect sensitive business information from modification, disruption, destruction, and inspection.Information security refers to the protection of digital data and systems from unauthorized access, use, disclosure, disruption, modification, or destruction. It encompasses a range of measures, including policies, procedures, technologies, and practices, aimed at safeguarding sensitive information. Information security aims to ensure the confidentiality, integrity, and availability of data, preventing breaches and unauthorized activities. It is vital for organizations to implement robust information security measures to protect their assets, reputation, and stakeholders' trust.
Information security management has become essential, as, with every new application, newer vulnerabilities crop up, posing immense challenges to those who are mandated to protect the IT assets.
Information security, often referred to as InfoSec, refers to the processes and tools designed and deployed to protect sensitive business information from modification, disruption, destruction, and inspection.
Netrika is CERT-In empanelled for providing an IT security audit.
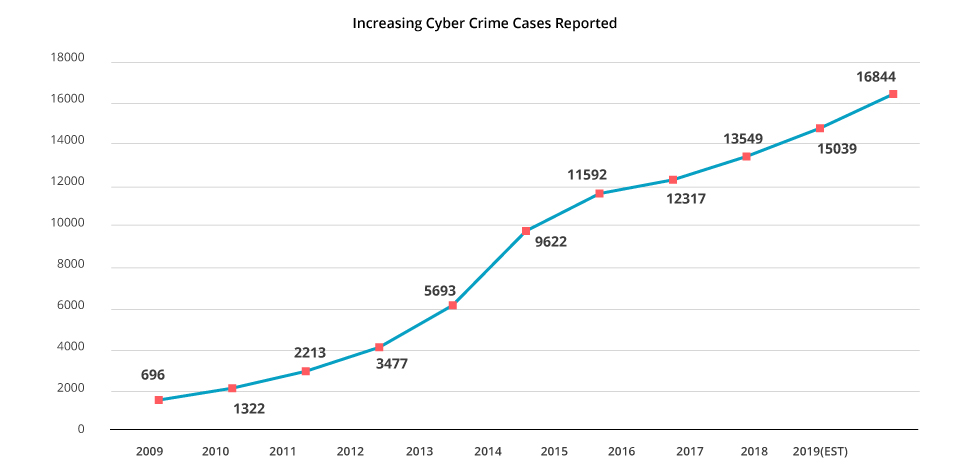
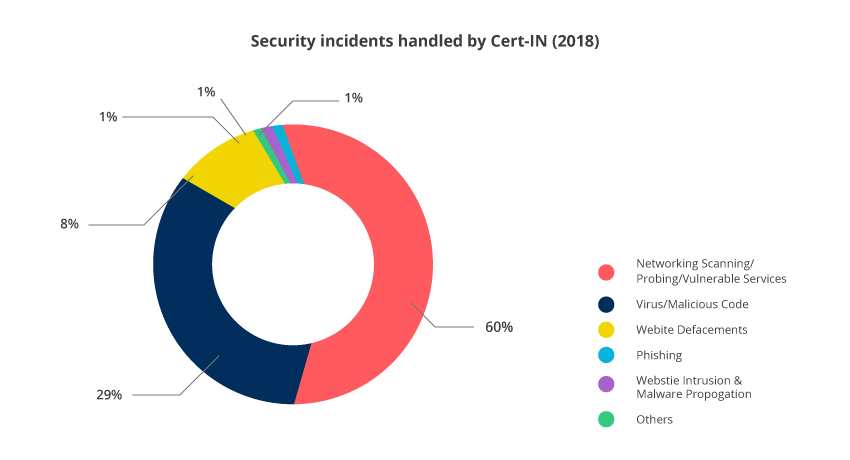
Netrika gauged the increasing threat of cybercrime and conducted a detailed survey to understand awareness about cyber-crime and information security across the industries
ISMS/BCMS Implementation & Certification, Web/Mobile Application Security, GDPR Project Management, Compliance Vendor Risk Management, Information Security Awareness & Training, Cyber Security Framework, Strategy and Program Transformation BCP Policy, Process and Plan Along with Test Reports Gap Assessment and Risk Assessment Cyber Threat Assessment.
The network strength and security of the systems in a company or business are of great importance. In spite of this, a lot of businesses do not bother with this and take their chances. It is a foolish decision because of the sheer number of cyber- attacks that take place with regularity, and the high intelligence of hackers with harmful intentions. The exposure of valuable customer details can spell doom for any organisation, and it is absolutely essential to avail of IT security services.
Security risks are present from both outside as well as inside the company. They have the potential to bring a business down to its knees, from which they can never fully recover. Add to it the prospects of shareholding devaluation and lost credibility, and it making for a very sorry picture. In recent years, the definition of security and network systems has undergone a sea change, and no company can afford to sit back on its laurels, waiting for a crime to happen.
Business owners install protective measures like anti-viruses, firewalls and IPS; these security tools are not enough to safeguard company interests. A lot of companies do not have the time to devote to security assessment, and this is where 24/7 security team from a third party are useful.
A chain is as strong as its weakest link. And in an organisation, especially in the Information technology arena, security is paramount. An IT security audit goes a long way in ensuring the owners of the company as well as the stakeholders that all is well on board.
An IT security audit comprises both the checking of the physical and the virtual data security. Physical access to data, the person who accesses the data and does it in the right way, as well as a thorough checking of virtual data is what Netrika does for its customers around the world.
Information security, often referred to as InfoSec, refers to the processes and tools designed and deployed to protect sensitive business information from modification, disruption, destruction, and inspection.
Generally, an organization applies information security to guard digital information as part of an overall cybersecurity program. Infosec ensures that the employees have access to the data they require, while preventing unauthorized access. It can also be associated with risk management and legal regulations.
Information security or infosec is concerned with protecting information from unauthorized access. It's part of information risk management and involves preventing or reducing the probability of unauthorized access, use, disclosure, disruption, deletion, corruption, modification, inspection, or recording.
Since cybercrime is evolving at such a rapid pace, the top concern regarding security is what are the best practices and what constitutes good cyber security.
It is crucial to raise employee understanding of proper cyber hygiene when using the company network and the resilience of the network’s architecture. Instilling healthy practices concerning things like strong password policies, preventing access to protected company networks via insecure personal devices, and mixing personal documents and emails with business-related ones are all examples of excellent cyber hygiene.
An information security management system (ISMS) is a set of policies and procedures for systematically managing an organization's sensitive data. The goal of an ISMS is to minimize risk and ensure business continuity by proactively limiting the impact of a security breach.